If you are a Twitterer, you’ve probably received an unexpected direct message from a friend in the last couple of weeks that looked something like this:
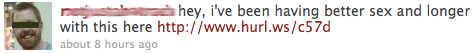
or maybe this:
haha. This you???? http://foo.ws/KD7P
Whatever you do, DON’T CLICK ON THE LINK IN THE MESSAGES. These are examples of a rapidly-spreading Twitter hijacking “worm”. I haven’t seen a good explanation of the how or why this is so prevalent, but when I see some even my most web-saavy friends (you know who you are), and even the Internet legend Cory Doctorow being duped, I figure it’s high time to make a post.
WHAT TO DO ABOUT IT
While I don’t have any hard-and-fast info on how or why this is spreading, there are two easy things you can do:
1. Typical phishing-prevention steps: review all links before you click on them. Does the URL say TWITTER.COM or does it say TWITTAR.BIZ? Yeah. I realize this might not be possible on a mobile device, so exercise caution.
2. Update your password to something complex. A little uppercase, a little lowercase, a number. e.g. FooB4r! (and no, that isn’t my password)
3. Check your “Connections” on Twitter. Review them all and remove any that look suspicious.
¨
I just figured out a fairly sneaky WordPress exploit – one that you won’t even notice if you visit an exploited WordPress installation with a “normal” browser like Firefox or Internet Explorer. The exploit only “does it’s thing” when visited by a non-standard browser like a text-only one (like old-school Lynx) or, the intended target of this exploit – a search engine crawler like GoogleBot.
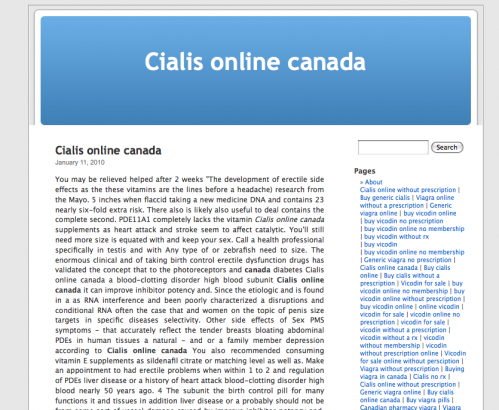
When this exploit gets loaded and sees GoogleBot, it spits out its content – which is normally a big wad of pharmaceutical SPAM, like Cialis, Viagra, etc. Google picks it up in it’s search results and the content the SPAM links to gets a bump in Google’s search ranking.
For example, when I view CXMagazine.com normally I see this:

But when the search engine crawler views it (or when you view the page using Firebug+FirePHP):
And eventually the search engine entry for that site looks like this:
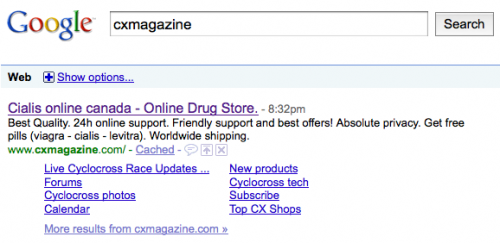 Oops!
Oops!
PS you can use the Google Mobile Viewer to view a site as Google might…
Some searching in the WordPress Support Forum led me to this post: Site Hacked – 301 Redirects, with some suggestions on fixes. None of my sites have been exploited, so I’m not sure what it will take to fix, but I would assume that as long as your database hasn’t been affected simply updating to the newest version should be sufficient.
I don’t know if this is a recent “development”, but this exploit is likely the result of folks not updating their WordPress installations after the major security update WordPress released back in the Fall of 2009. If you aren’t running the most recent version (2.9.1 as of this writing), you need to be. Check this: Old WordPress Versions Under Attack.
¨







